Zero-Day Protection: Block Unknown Threats
Attacks from unknown threats pose critical risks to businesses and are the hardest to prevent. This is why many businesses rely on SOC teams to detect them after breaching their systems. This is an ineffective strategy. Check Point’s evasion-resistant technology maximizes zero-day protection without compromising business productivity. For the first time, businesses can reduce the risk of unknown attacks by implementing a prevent-first approach.
TAKE OUR SECURITY CHECKUPQuantum Lightspeed: World’s Fastest Data Center Firewall Get E-Book
Effective Zero-Day Protection
![]()
Intelligence
Translates intelligence on Gen V threats into proactive security intelligence
![]()
Prevention
Preventing attacks is a better strategy than detecting threats post-breach
![]()
Consolidation
Unified architecture blocks modern attacks across all vectors
A Guide for Adopting a Threat Prevention
Approach to Cyber Security
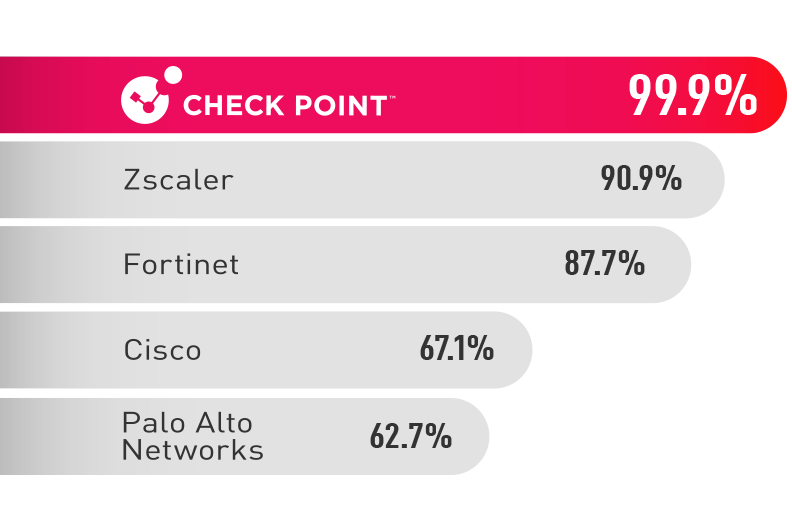
Our Threat Prevention Sets Records
For the third year in a row, Check Point achieves the industry’s highest threat prevention rates across all categories in Miercom’s 2025 Enterprise and Hybrid Mesh Firewall Security Report.
Our Infinity Platform offers the best protection against the latest generation of cyber attacks, with a block rate of 99.9% on new malware, 99.7% phishing prevention rate, and 98% average block rate on high & critical intrusion events.
Check Point Provides Zero-Day Protection Across Its Network, Cloud, Users and Access Security Solutions
A Strategy for Improving Security Efficiency:
Achieve Better Security and Lower Costs with Consolidation

ThreatCloud AI: The Power
of Shared Intelligence
ThreatCloud AI is Check Point’s rich cyber defense database. Its threat intelligence powers Check Point’s zero-day protection solutions.
WATCH THE VIDEOHow Artificial Intelligence Helps Deliver
Superior Threat Prevention
Threat Extraction Content Disarm and Reconstruction (CDR)
Threat Extraction removes risky features from files such as macros, embedded objects and more, rather than determining their maliciousness. By cleaning the file before it enters the organization.
READ MORE
Core Threat Prevention Engines
![]()
CPU-level Threat Prevention
- Evasion-resistant, zero-day exploit identification
- Patented CPU-level technology is virtually impenetrable, even by nation states
- Detects and blocks malware before evasion code can execute
![]()
Threat Emulation
- Highest accuracy scores in industry tests
- Rapid verdicts in milliseconds
- Comprehensive coverage of attack tactics, file-types, and operating systems
![]()
Threat Extraction
- Sanitizes files to prevent threats
- Proactively blocks malware
- Delivers reconstructed and safe files in seconds
![]()
AI-Powered Engines
- Artificial intelligence delivers state-of-the-art threat prevention
- Analyzes thousands of threat indicators to produce accurate verdicts
- Provides insights to help expose new malware families
![]()
Anti-Ransomware
- Prevents online extortion attacks
- Automatically restores files encrypted by an attack
- Works in both online and offline mode to automatically restore files
![]()
Anti-Phishing
- Blocks access to phishing websites
- Alerts when credentials are re-used
- Prevents account takeover
Infinity Consolidates
Security Across Vectors
Check Point Infinity is a unified security architecture that delivers real-time threat prevention of both known and
unknown threats, simultaneously protecting the network, cloud, endpoints and mobile and IoT devices.
Proven, Tested and Trusted
2023 Cyber Security Report
Geo-political conflicts trigger all-time high for cyberattacks.
See more trends and insights.

Additional Resources
Downloads
The Next Cyberattack Can Be Prevented
CISO Guide to Mobile Threat Defense
Ransomware: a New Approach to Identifying, Blocking and Real-time Remediation
Videos
Understanding Malware DNA: The Classification of Malware Families
Five Best Practices to Reduce your Cybersecurity Risks
Check Point Threat Extraction for Web Technology
SandBlast Mobile Defeats Cyberattacks
Check Point Presents: Latest Developments in the World of Cryptojacking
Check Point SandBlast Agent: Advanced Endpoint Protection & Forensics
Links
Check Point’s Threat Emulation Stops Large-Scale Phishing Campaign in Germany
Maximum Zero-Day Prevention Without Compromising Productivity
Introducing Malware DNA: Gaining Deep Insights into Malware Ancestry
SandBlast Agent Protects Against BlueKeep RDP Vulnerability












